Accurate Insider Threat Detection
The Most Important Criteria in a Detection Solution is Accuracy
TrackerIQ’s unique analytic approach achieves high accuracy using the activity’s context by analyzing a sequence of activities, instead of the activity itself. It is based on the underlying assumption that an abnormal session is characterized by a journey which isn’t similar to the user’s typical journeys in an application.
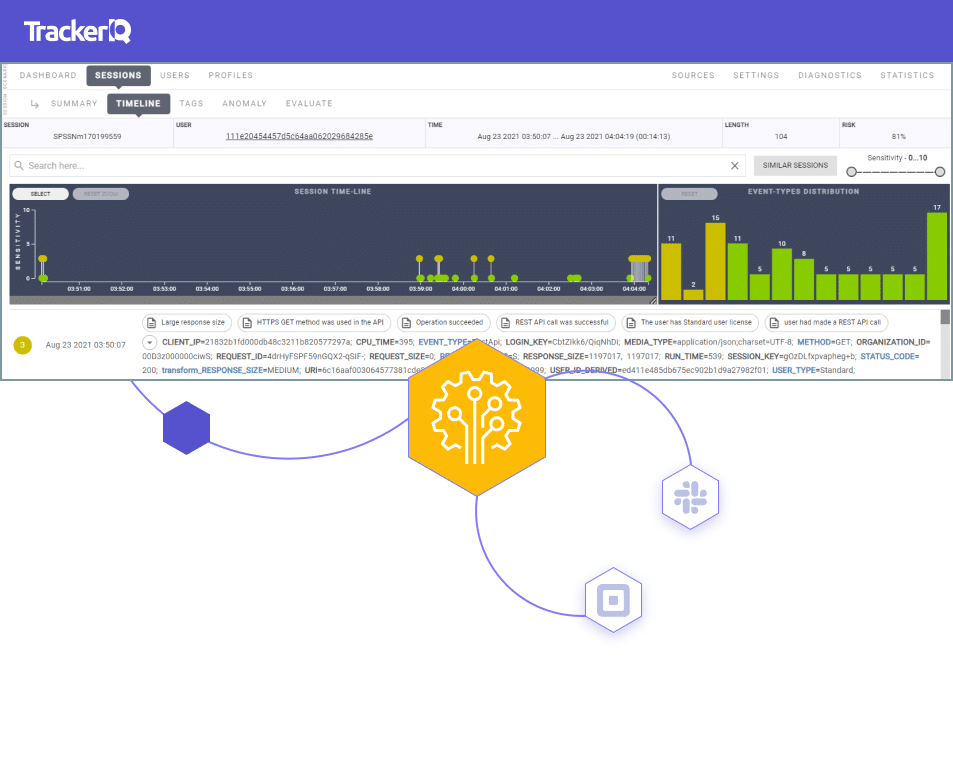
User Journey Analytics
A user journey is the sequence of activities performed by a user in an application. Tracking user journeys enables a far more accurate and comprehensive level of application detection.
While User Behavior Analytics is about a single baseline for each activity and an analysis of each activity on its own, User Journey Analytics learns for each user the complete set of typical user journeys in an application by looking at sequences of activities.
An impersonator would need to imitate a user’s normal journey in an application in order to succeed, and insiders looking to misuse or abuse an application will ultimately deviate from their normal user journey profiles.
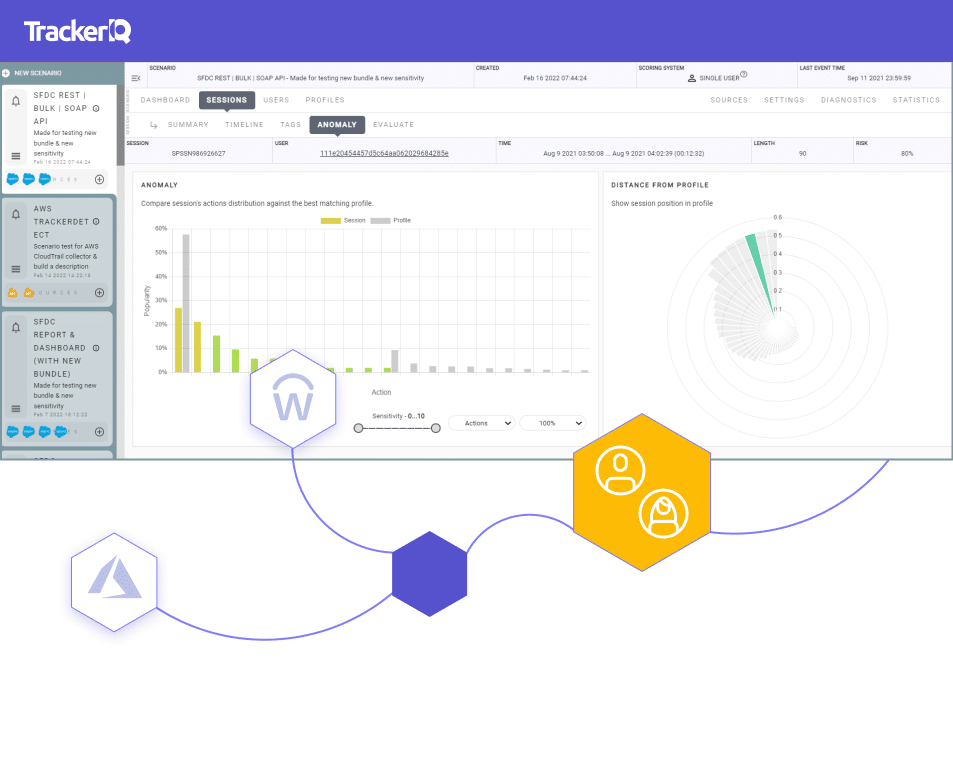
Applying Machine Learning to Learn the User Journey Profiles
The challenge is of course how to learn automatically all the typical user journeys in an application (or even across applications) as each user has many typical journeys profiles. It is important to emphasize that there is no meaning to an average journey. We must learn all the user’s typical journeys to accurately detect the abnormal journey.
To accurately learn user journey profiles, TrackerIQ reads log events and generates user journeys (i.e. the user sessions in the application). It then groups similar user journeys together to generate the user’s journey profiles. To perform this grouping of journeys accurately, RevealSecurity has developed a unique clustering engine. Based on the groups generated by the clustering engine, TrackerIQ generates user’s journey profiles and uses them to detect abnormal journeys.
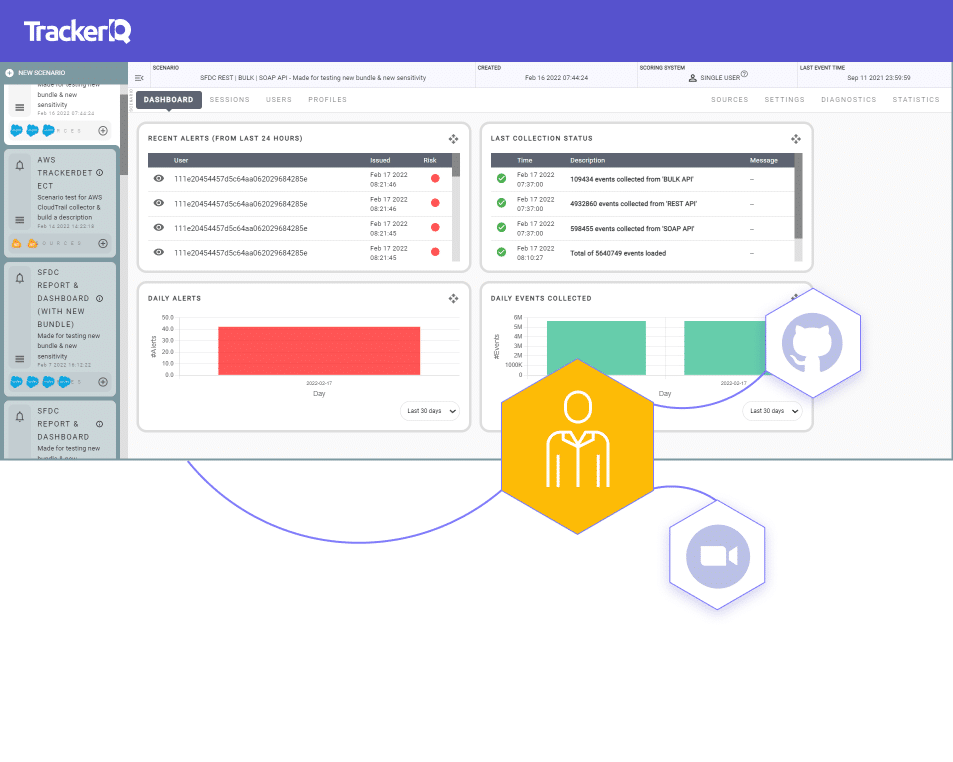
Ubiquitous Detection Model: The Essence of Activities Makes No Difference to TrackerIQ
TrackerIQ’s detection is based on the user journey characteristics, i.e. the activities performed during a user journey, the order in which they have been performed and the time difference between them. These user journey characteristics are completely indifferent to the meaning of application layer activities. Thus, TrackerIQ’s detection model can be applied to any application because it is ubiquitous and agnostic to the meaning of an application’s activities.
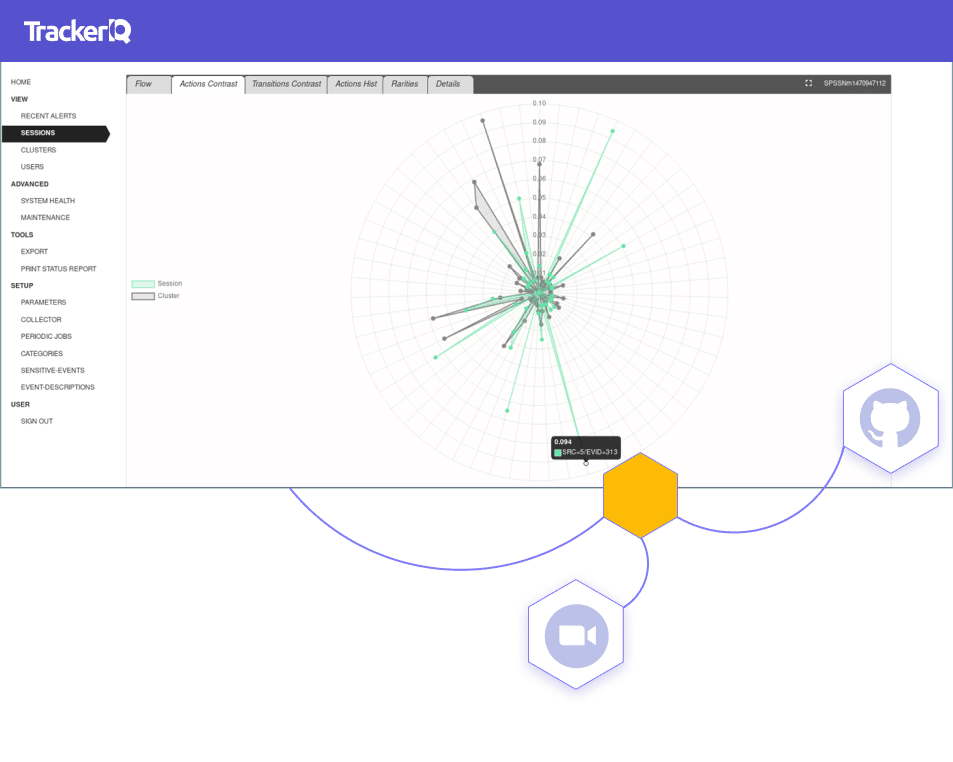
RevealSecurity's Clustering Engine
Most clustering engines in the market suffer from at least a 10% margin of error, which isn’t acceptable when clustering results are intended for cybersecurity anomaly detection. Classical clustering engines also require the cleansing of outliers, while these outliers are what TrackerIQ is looking for in anomaly detection.
RevealSecurity developed a unique clustering engine tailored for sequence clustering. It doesn’t require prior knowledge as to how many clusters to generate, and is also extremely accurate, while still almost linear in the number of data points it clusters. The engine detects outliers – removing them from the data set to enhance clustering accuracy, while also identifying these outliers as anomalies. Thus, the same clustering engine that generates groups of similar user journeys, also detects abnormal user journeys and reports them as anomalies in historical data used for learning normative user journeys.
Application Agnostic
TrackerIQ’s detection model is based on a ubiquitous user journey model which is applied on any business application and across applications: IT, OT and SaaS.
Accurate Detection
TrackerIQ analyzes user journeys (i.e. application sessions), not individual activities, and the journey provides a context which is important for accurate detection.
User Journeys
TrackerIQ analyzes user journeys, not individual activities. It applies clustering to group similar sessions together and then generate a typical user journey from each such group of similar session.
No rules required
Rules detect only known patterns, while attackers are constantly leveraging loopholes. Evolve to survive.
