© 2025 Reveal Security. All Rights Reserved.
Reveal goes where traditional tools stop – and into what happens after an identity successfully authenticates.
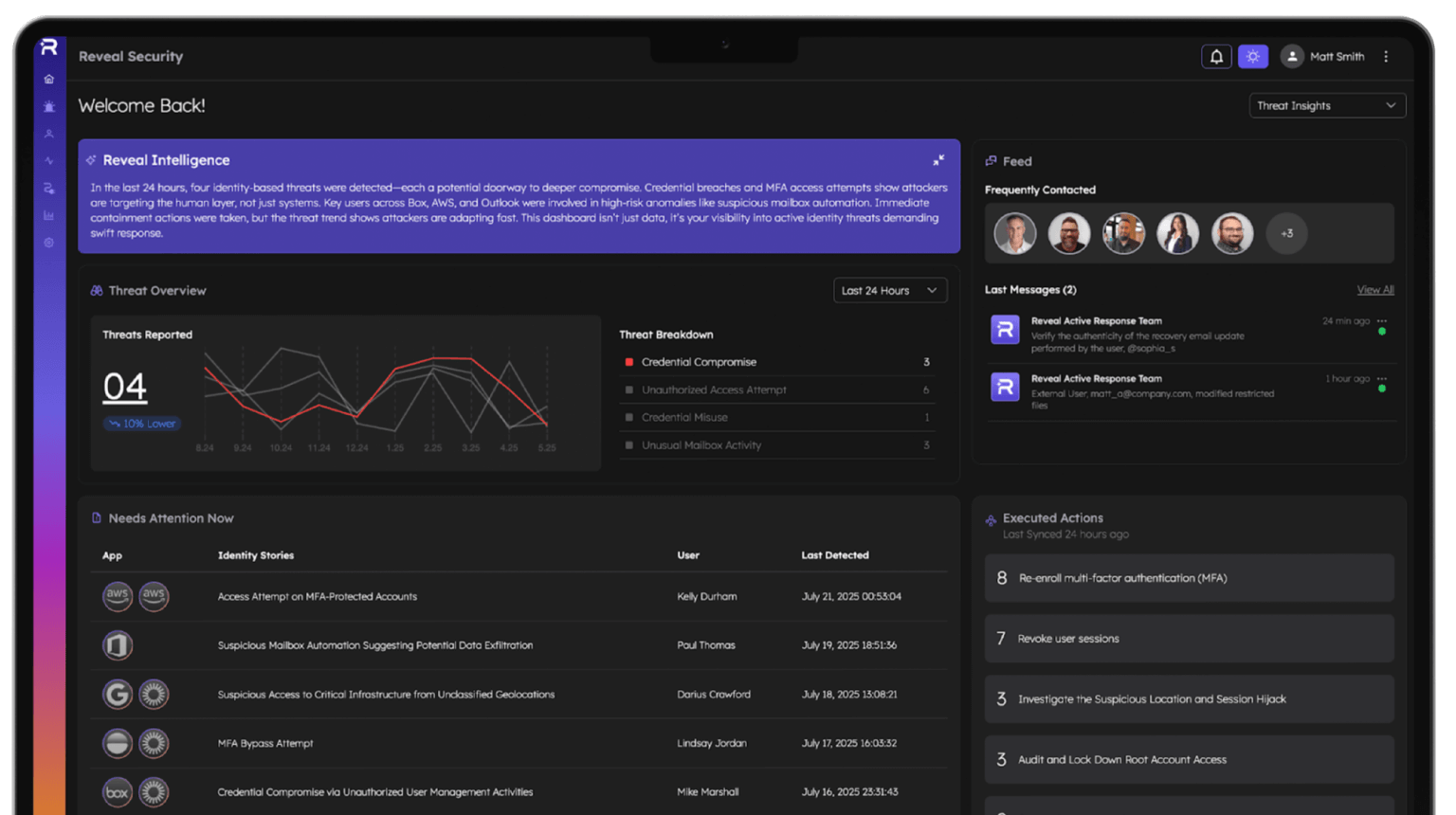
Reveal detects imposters and malicious insiders by monitoring identity stories across enterprise applications using behavioral identity analytics.
Stop them before they strike.
Trusted By






Why Reveal?
Reveal makes monitoring your applications easy.
With rich data, application threat modeling, ML and AI, Reveal protects against account takeover attacks and insider threats without burdening the SOC with alerts or the need to write detection rules.
Complete Visibility
of identity behavior across SaaS, cloud and custom apps
Monitor All Identities
Human, Non-Human, AI
Accurate Detection
of threats reduces analyst workload
Real-time Response
like automated session revocation or account suspension
Preemptive Action
based on identity attribution and predictive intelligence
Simple & Seamless
Activate existing data sources. No new agents or rules.
Detect Credential Abuse
Insider Threat Protection
Human & Non-Human Identity Behavior Monitoring
SaaS Security
Cloud Security
Preemptive Cyber Defense
Use Cases
Detect Credential Abuse
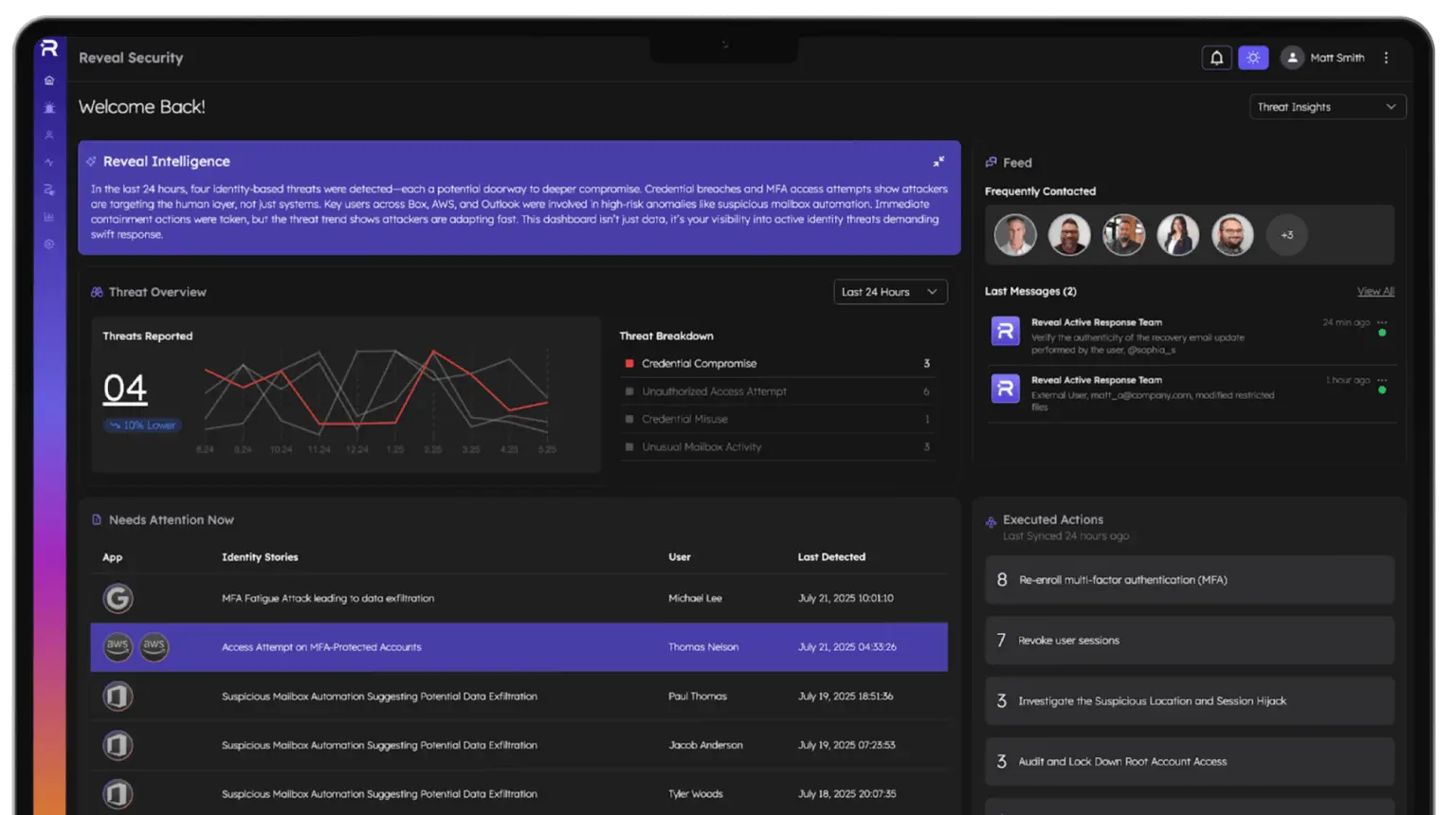
Detect Credential Abuse
Identify unauthorized access and post login activity resulting from stolen or exploited credentials.
Insider Threat Protection
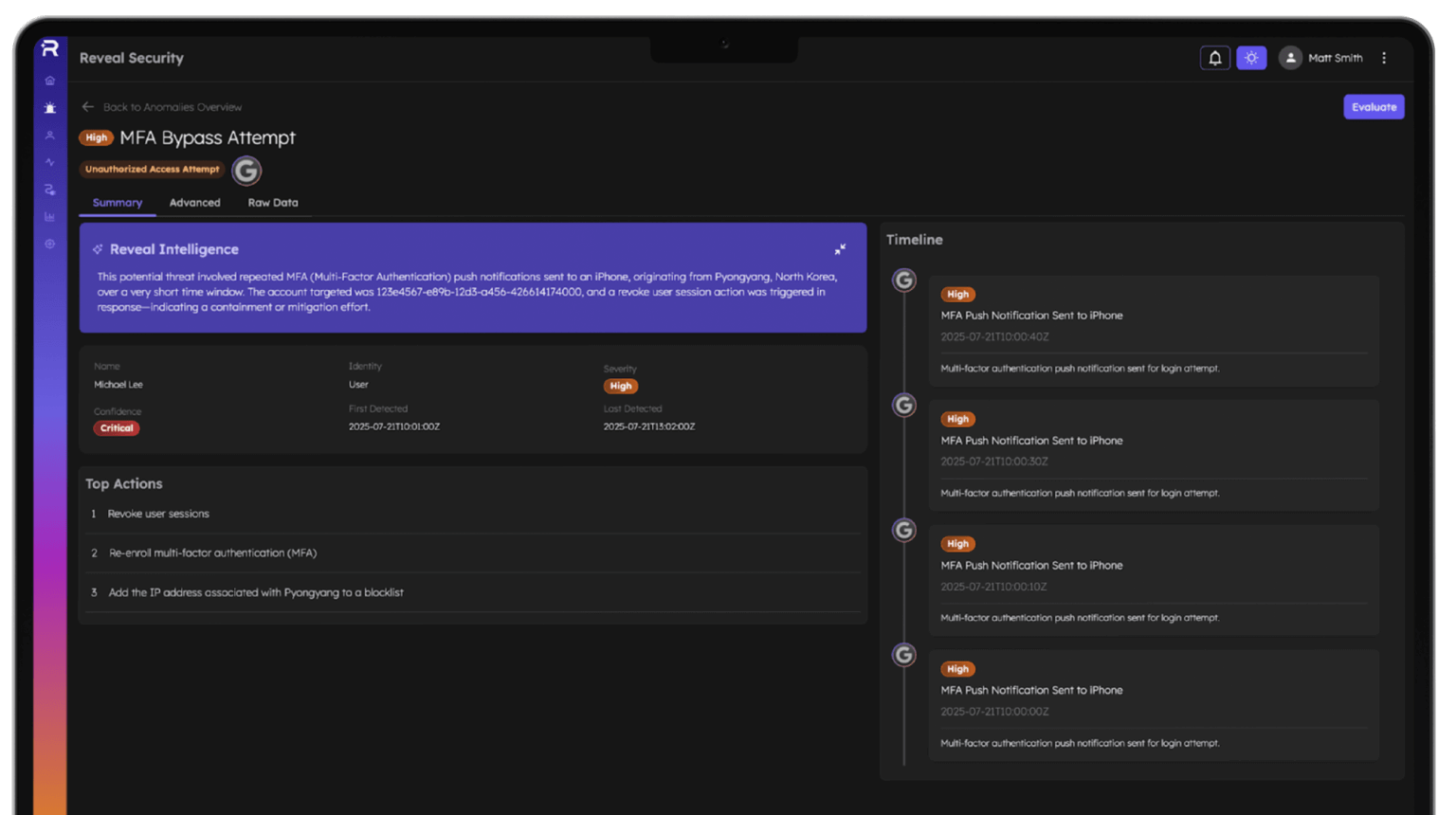
Insider Threat Protection
Detect malicious, negligent, or compromised insiders.
Human & Non-Human Identity Behavior Monitoring
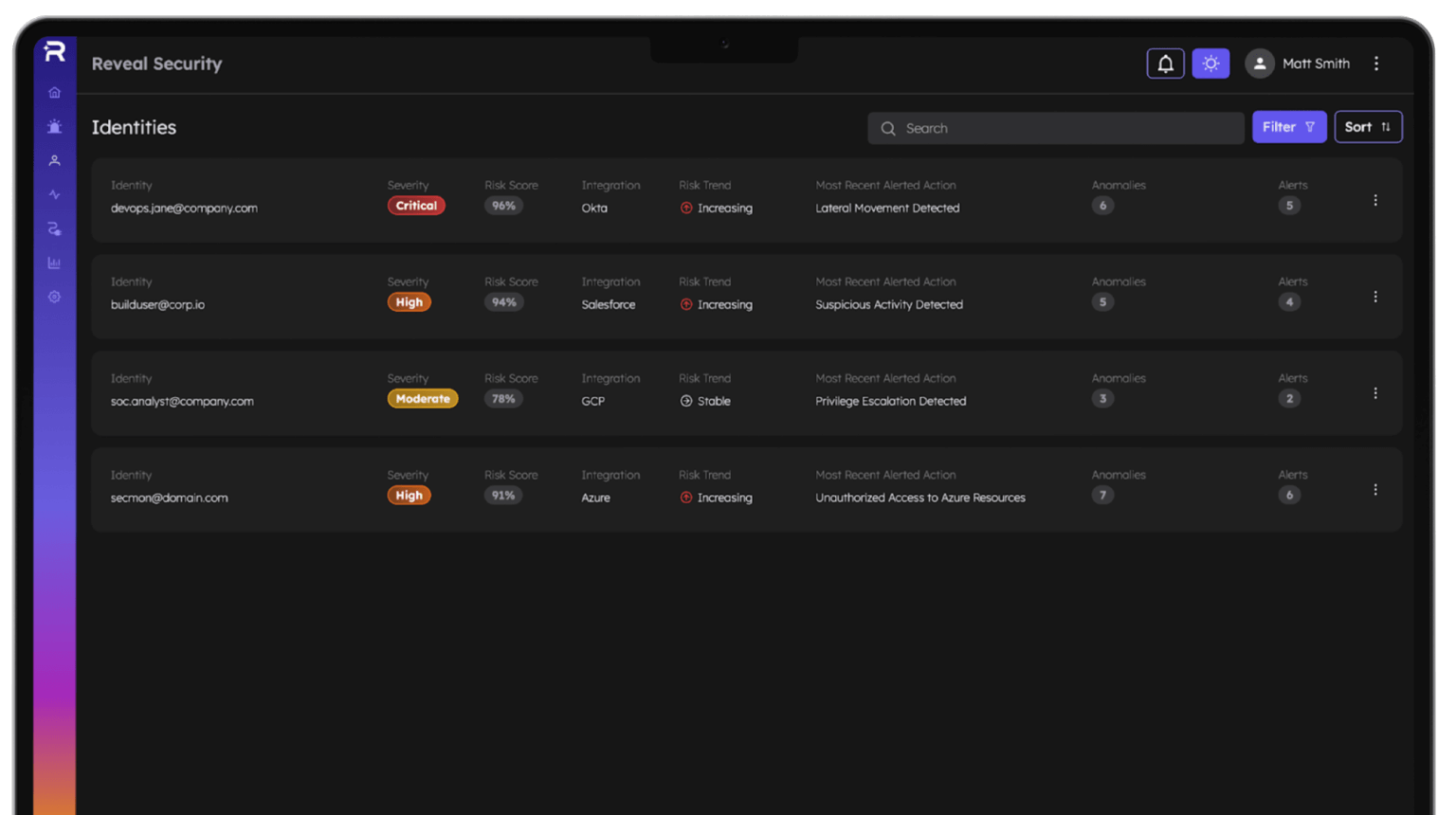
Human & Non-Human Identity Behavior Monitoring
Monitor any identity type.
Human, non-human, AI.
SaaS Security

SaaS Security
Gain visibility and detect unusual activity in third-party SaaS and custom applications.
Cloud Security
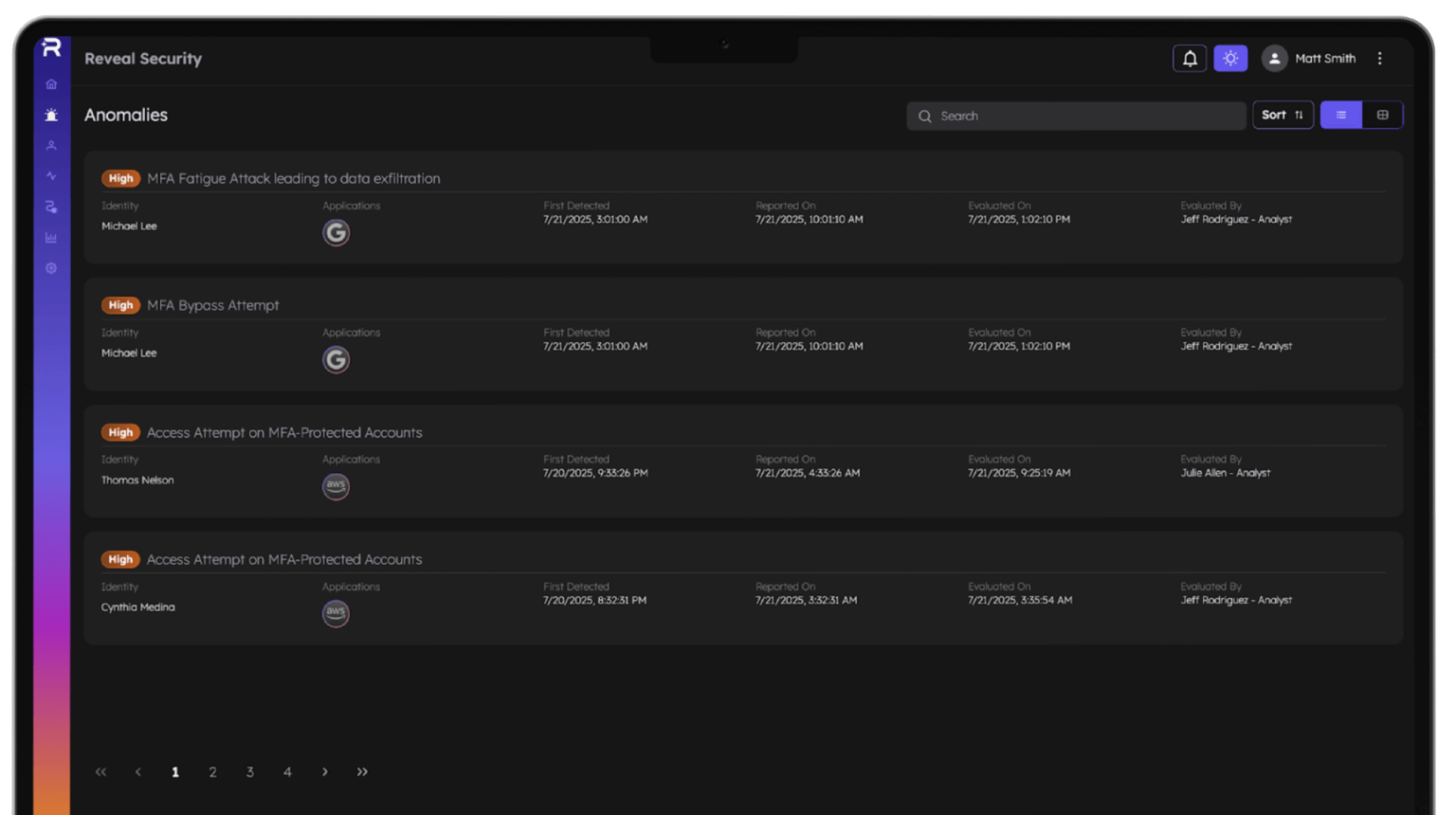
Cloud Security
Monitor privileged user activity in the cloud.
Preemptive Cyber Defense
Preemptive Cyber Defense
Move from detection to attack anticipation and proactive response centered on identity behavior.

CISO, LifeLabs
Mike Melo
With Reveal Security, we get an extremely accurate representation of how our users and identities are interacting with our data and application systems.

Head of Poste Italiane’s CERT
Nicola Sotira
We saw something with Reveal that standard tools missed. We caught the anomaly before it created damage.




