Detect and respond to account takeover attacks
Detect the use of stolen credentials quickly to minimize business disruption and damage
Book a Demo
Hijacked trust is a threat actor’s best weapon
Threat actors have learned that the best way to breach a high-value target and advance an attack is by stealing the credentials of a legitimate user or identity.

Even though most organizations have mature identity and access management (IAM) tools and best practices like multi-factor authentication (MFA) in place, they often trust users implicitly once they have been authenticated successfully.
The problem is that motivated threat actors remain highly effective at finding new and creative ways to circumvent preventative identity controls.
86 percent of successful web application breaches involve the use of stolen credentials.
Source: “2023 Data Breach Investigations Report,” Verizon, June 6, 2023.
Monitoring the behavior of authenticated identities speeds detection of account takeovers
While investing in IAM and other preventative identity protection measures like privileged access management (PAM) is essential, these technologies are far from infallible. Security teams must continue to scrutinize the behavior of identities continuously after the point of authentication. And unfortunately, traditional detection can’t distinguish between legitimate identities and identities that have been compromised by an external attacker.
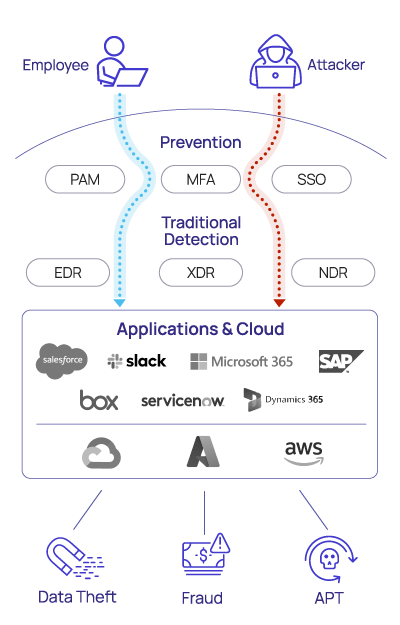
The most effective account takeover techniques are novel in nature and cannot not be detected by pre-defined detection rules.
Identity Journey Analytics™ is the key to detecting compromised identities
The Reveal Security platform uses a patented technique called Identity Journey Analytics™ to monitor identity behavior and analyze their journeys after login. Using unsupervised machine learning, Reveal Security automatically learns the typical journeys and analyzes ongoing journeys for anomalies, which are strong indicators of credential misuse resulting from a compromised identity.
Through its unique ability to distinguish unsanctioned application usage from normal behavior, Reveal Security can quickly and accurately identify instances when identities are being used for malicious purposes, including privileged users such as admin and super admin accounts.
Reveal Security integrates with your full array of business applications, including widely used software-as-a-service (SaaS) platforms and API-based communication, turning disparate log events into a normalized view of a journey that is analyzed holistically to accurately detect anomalies.
Minimize damage when identities are compromised
For most organizations, an identity based attack is a matter of when – not if. And if it’s not caught quickly, the business impact can be extensive. Financial loss, reputational damage, operational disruption, and intellectual property leakage are common outcomes.
By detecting compromised identities quickly, and providing the entire user journey, Reveal Security enables security teams to accelerate their investigation, response, containment, and recovery so negative business impacts are minimized as much as possible.

Empower your security team instead of overwhelming them
The Reveal Security platform is easy to implement across all of your applications, whether they are software-as-a-service (SaaS), on-premises, or cloud-hosted. There are no manual detection rules to create.
No rules also means no endless wave of false positive alerts. Instead of drowning in noise, your team can focus on the activity that matters most and respond quickly with the help of clearly communicated findings and guidance.

Strengthen your risk posture with identity-based attack detection across SaaS and cloud
The Reveal Security platform’s unique capabilities provide a critical complement to your preventative identity protection measures.
Accelerate identity compromise detection
Detect abnormal activity quickly, so you can respond before a material breach or other negative business impact occurs.
Find attacks that rule-based detection misses
Protect your organization against novel attack techniques that leverage compromised credentials and can’t be anticipated with rules.
Optimize team focus and efficiency
Minimize false positive alerts and give responders the insights and guidance they need to act quickly.
Learn more about how Reveal Security detects account takeover attacks
View more
WHITEPAPER
Safeguard Your Organization Against Account Takeover Attacks
Attackers increasingly are using stolen credentials to target data in enterprise SaaS applications and cloud. Are you prepared?
Download
SOLUTION BRIEF

