Protect your
applications against
insider threats
Speed detection of insider threats before they become substantial security incidents to reduce financial loss and business disruption.
Book a Demo
Insider threats come in many forms
Most organizations put significant effort and investment into protecting applications from external threats, but insider threats are often less of a focus. And they can come in many forms.
Malicious
Insider
Intentionally uses their access to harm the organization
Negligent
Insider
Compromises company data and systems unintentionally
Misdirected
Insider
Exploited by an attacker to gain system access
Compromised
Insider
Account has been taken over by an attacker
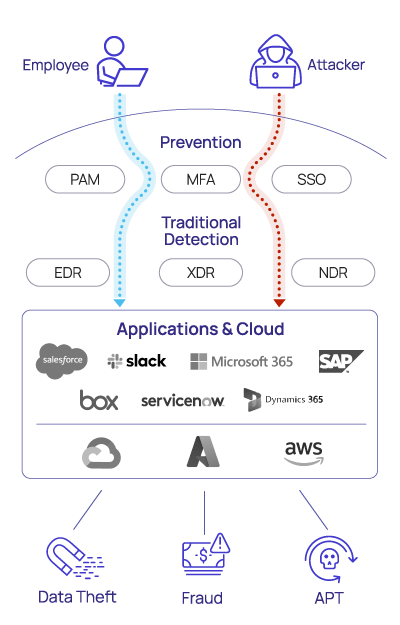
Authenticated identities are at the forefront of insider threats
Traditional security approaches often trust authenticated users implicitly and aren’t capable of distinguishing between normal and unsanctioned application usage after login.
Identity Journey Analytics™ is essential to detecting insider threats
The Reveal Security platform which is based on patented Identity Journey Analytics™, powered by unsupervised machine learning, monitors and analyzes user and identity journeys. The platform learns their typical journeys within and across business applications that represent normal behavior.
New journeys are compared to the typical journeys learned to accurately distinguish between normal and unsanctioned application usage and flush out all types of insider threats

Monitor privileged users and administrators
Insider threats related to privileged users, IT admins and super admins can have a significant impact on your business.
Reveal Security conducts comprehensive monitoring of administrators and other privileged users’ activities, and detects anomalous behavior to identify malicious or negligent admins and compromised administrator accounts.
Insider threats are in every business application.
So should your security coverage.
Reveal Security does not require manual rule creation to detect insider threats, so it is fast and simple to apply across all your business applications including SaaS, commercial, open source, and customer applications for complete coverage.















![]()
![]()
![]()

![]()
Apply consistent detection and response for all insider threats
Reveal Security can cover all applications, positively impacting your security and operations teams in several ways.
Accelerate time to Detection
Reduce MTTD for insider threats from months to a few hours, reducing the likelihood that they will escalate into a major incident.
Detect novel attacks
Analyzing identity behavior and journeys is ideal for detecting novel attack techniques vs. other solutions that use rule-based detection methods.
Reduce false positives
High accuracy and high fidelity alerts improve operational efficiency. Shift from hundreds of alerts of ambiguous validity and criticality down to 1 per week.
Learn more about Reveal Security for insider threats
View more
WHITEPAPER
Protect Your Applications and Cloud Services Against Insider Threats
Learn about the full range of insider threats, how to identify the critical gaps in existing solutions, and how new solutions focused on insider threat detection in applications and cloud can play a pivotal role in efforts to stop insider threats.
Download
SOLUTION BRIEF

