Identity Journey Analytics™
Learn about the innovative technology that powers the Reveal Security platform.
Book a Demo
Our Patented Technology
Identity Journey Analytics™
Reveal Security’s patented Identity Journey Analytics™ uses unsupervised machine learning to learn the usage patterns or typical “journeys” of human and machine identities in and across applications and uses it to accurately detect anomalies.
What is an Identity Journey?

Why are Identity Journeys important?

How is Identity Journey Analytics different?
Identity Journey Analytics enables the Reveal Security platform to deliver highly accurate detections and orders of magnitude fewer alerts than event-based detection solutions, i.e. correlation rules and UEBA .
Identity Journey Analytics
Identity Journey Analytics analyzes “journeys” or the sequences of actions for each identity and learns the complete set of typical journeys for that identity. When an abnormal journey is detected, it is always worthy of investigation.
UEBA
Event-based detection tools like User Behavior Analytics (UBA/UEBA) create a single baseline for each action per user and an analysis of each action on its own. This approach creates a high volume of alerts with high false positive rates.
Identity Journey Analytics
Identity Journey Analytics analyzes “journeys” or the sequences of activities for each identity and learns the complete set of typical journeys for that identity. When an abnormal journey is detected, it is always worthy of investigation.
UEBA
Event-based detection tools like User Behavior Analytics (UBA/UEBA) create a single baseline for each activity per user and an analysis of each activity on its own. This approach creates a high volume of alerts with high false positive rates.
How It Works
A universal model
- The actions performed by the identity
- The order in which these actions were performed
- The time intervals between the actions
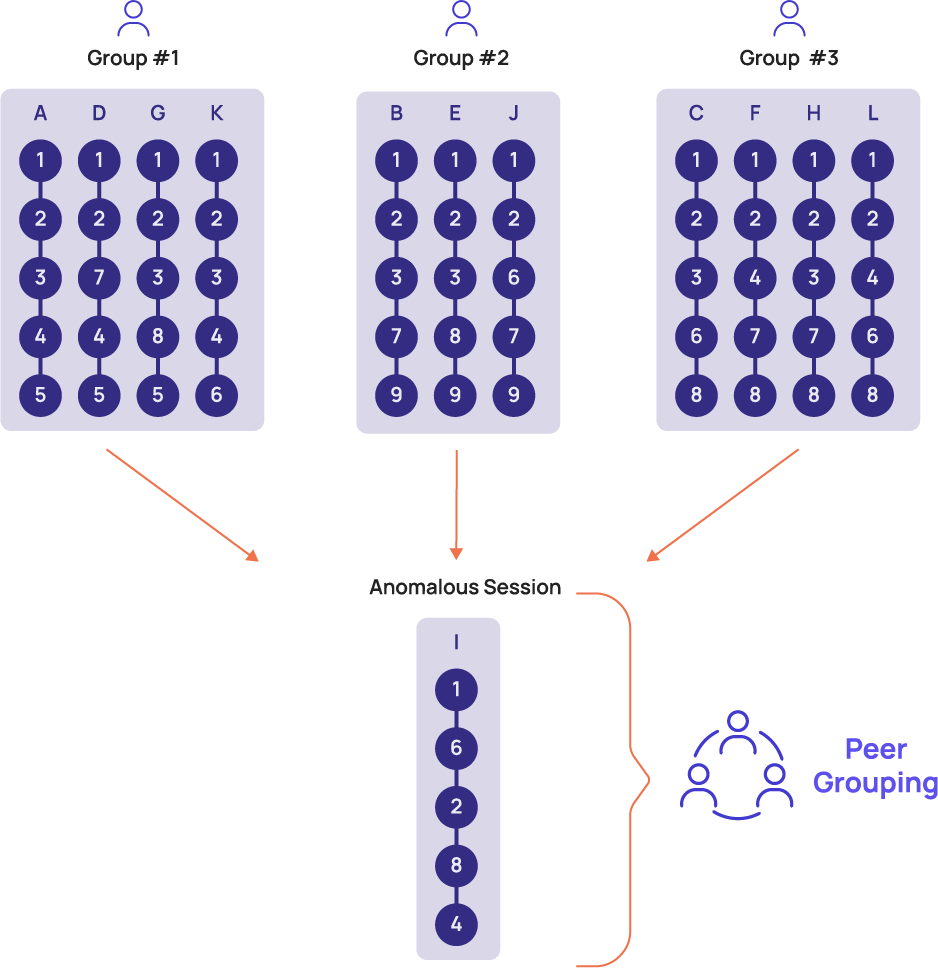
Learns typical identity journeys
Using a patented clustering technology, Identity Journey Analytics learns all the typical journeys per identity and for groups of identities. The clustering technology is used to accurately and efficiently group similar journeys together, and then the platform builds a typical journey from each group of similar journeys.
To detect scenarios in which identities behave differently than their ‘peer’ group, the platform also compares each identity journey against typical journeys learned for the cohort to which the identity belongs.
Sequence clustering engine detects anomalies
Identity Journey Analytics uses a clustering engine tailored for sequence clustering. The same clustering engine that generates groups of similar identity journeys, also detects abnormal journeys, and reports them as anomalies in historical data used for learning normative journeys.


Accurate detection
Identity Journey Analytics is what drives the high accuracy of the Reveal Security platform. By correlating the journey anomaly scores with additional data and capabilities in the platform, anomalies are scored, prioritized and delivered to the security team with the context they need to investigate and respond quickly.
To go deeper into our innovative technology, read the whitepaper.
Get the Whitepaper
Identity Journey Analytics is the innovation that powers the Reveal Security platform.
empower your security team
Learn about the Platform
Request a Demo
Dive deeper into what makes Reveal Security the smart approach to detecting insider threats and identity-based attacks threats in applications and cloud services.

