Reveal Security Platform
Harness the power of unsupervised machine learning based behavioral analytics to detect insider threats and identity-based attacks in applications and cloud.
Detect, investigate and respond to identity-based attacks in SaaS, cloud and on-premises
Reveal Security empowers an identity-first approach to protecting critical data in your application environments by enabling you to quickly detect and respond to attacks that involve credentialed users and entities. The Reveal Security platform continuously monitors the behavior of human and machine identities operating in and across any application – SaaS, cloud and on-premises – and detects suspicious or malicious activity.
Detections are focused on activity within the application, where preventative identity systems and traditional detection solutions have little-to-no visibility. Our customers use the Reveal Security platform to detect and stop account takeover attacks and insider threats and minimize third-party risk.
Key platform capabilities
Gain visibility into identity behavior in applications
The Reveal Security platform continuously monitors identity behavior and gives you visibility into how identities behave in applications before and after login.Using unsupervised machine learning, it automatically learns the typical usage patterns of an identity or group of identities. These typical usage patterns become the basis to accurately distinguish between legitimate and suspicious behavior.
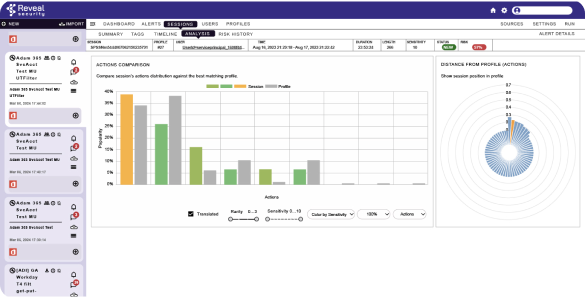
Identify anomalous behavior to accurately detect threats
Accuracy is arguably the most critical capability for a detection solution. Reveal Security’s patented Identity Journey Analytics™ learns the typical journeys in and across applications based on an identity’s actions, the order in which they were performed and time interval between them.
The Reveal Security platform learns typical journeys and creates normal journey profiles. It accurately detects abnormal journeys, which typically indicates an insider threat or an identity-based attack.
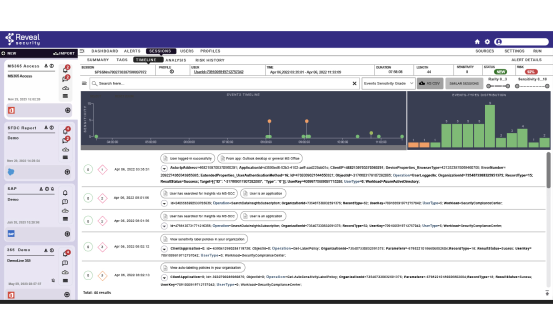
Speed threat investigation and response
Reveal Security provides unmatched context in every alert to speed investigation and response. In addition, Reveal Security translates the log events into human readable language to enable the SOC analysts to easily understand the meaning of each log event and focus on the important actions during the journey.
This ensures the suspicious behavior is clear, and next steps for SOC analysts are evident, without having to launch complex and time-consuming investigations to understand the incident.
Reveal Security integrates seamlessly with SIEM and SOAR solutions.
Strengthen your identity security posture
Reveal Security strengthens your organization’s security posture by providing valuable insights based on advanced analysis of the behavior of identities, both normal and anomalous.
With Reveal Security you can establish behavioral baselines, monitor privileged users, identify over-privileged users, discover credential abuse, and prioritize security risks effectively. These behavioral insights enable you to proactively detect and mitigate security incidents and enhance overall cybersecurity resilience.
Key platform capabilities
Gain visibility into identity behavior in applications
The Reveal Security platform continuously monitors identity behavior and gives you visibility into how identities behave in applications before and after login.
Using unsupervised machine learning, it automatically learns the typical usage patterns of an identity or group of identities. These typical usage patterns become the basis to accurately distinguish between legitimate and suspicious behavior.

Identify anomalous behavior to accurately detect threats
Accuracy is arguably the most critical capability for a detection solution. Reveal Security’s patented Identity Journey Analytics™ learns the typical journeys in and across applications based on an identity’s actions, the order in which they were performed and time interval between them.
The Reveal Security platform learns typical journeys and creates normal journey profiles. It accurately detects abnormal journeys, which typically indicates an insider threat or an identity-based attack.
Speed threat investigation and response
Reveal Security provides unmatched context in every alert to speed investigation and response. In addition, Reveal Security translates the log events into human readable language to enable the SOC analysts to easily understand the meaning of each log event and focus on the important actions during the journey.
This ensures the suspicious behavior is clear, and next steps for SOC analysts are evident, without having to launch complex and time-consuming investigations to understand the incident.
Reveal Security integrates seamlessly with SIEM and SOAR solutions.

Strengthen your identity security posture
Reveal Security strengthens your organization’s security posture by providing valuable insights based on advanced analysis of the behavior of identities, both normal and anomalous.
With Reveal Security you can establish behavioral baselines, monitor privileged users, identify over-privileged users, discover credential abuse, and prioritize security risks effectively. These behavioral insights enable you to proactively detect and mitigate security incidents and enhance overall cybersecurity resilience.
The Reveal Security advantage
Identity Journey Analytics™
Reveal Security is the only solution in the market based on patented Identity Journey Analytics™, that uses unsupervised machine learning to continuously monitor and analyze the behavior of human users, APIs and other entities in and across applications.
This approach delivers a superior level of accuracy and context, generates very few, accurate alerts, and enables the business to respond promptly before a material breach can occur.
Learn more
A universal model that works everywhere
Reveal Security’s unique Identity Journey Analytics applies to any application audit logs.
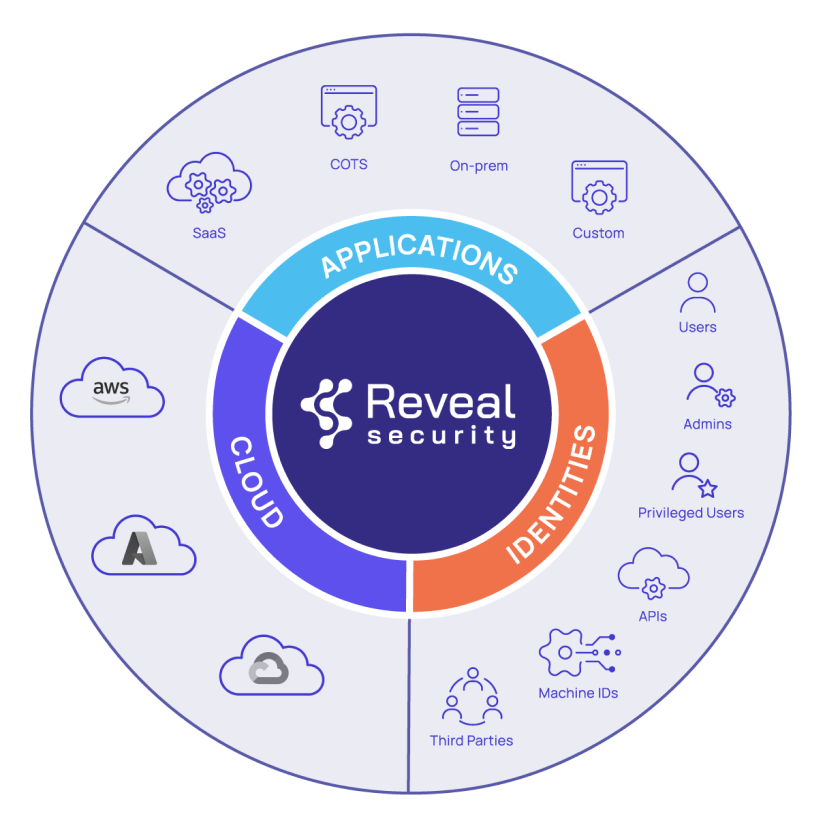
One solution across any application, anywhere
The Reveal Security platform is a single solution that works with human users, APIs and other entities, and works with and across any application and delivery model including SaaS, on-premises, custom-built and with any cloud service.
Business benefits
Improve SOC efficiency
Minimize financial
losses due to
breach
Lightning fast
time-to-value
Economies of
scale
Certified to keep your data secure



