ServiceNow provides a cloud platform for organizations to manage both internal and external IT operations. With a market share north of 50 percent, ServiceNow is one of the most popular IT service management platforms in the world.
Part of ServiceNow’s power stems from its ability to integrate with external systems via APIs. Enterprises routinely connect tens, hundreds, or even thousands of third-party applications, custom-built integrations and data sources to their ServiceNow instances.
But ServiceNow’s power and flexibility comes with the risk of malicious insider threats. Anyone inside an organization who can access ServiceNow – or an imposter taking over the identity of someone with credentials – can abuse access. They can leverage sensitive data and delete critical information both from ServiceNow, or from the various resources integrated with it.
Aware of these risks, ServiceNow has invested in multiple initiatives designed to help improve the platform’s security. Unfortunately, these native security features aren’t always enough.
Organizations looking to minimize the risk of attackers and malicious insider threats on ServiceNow should extend their security strategies beyond the platform’s built-in tooling.
ServiceNow External Attacker Scenario
Attackers Impersonating Insiders
A common attack vector is attackers impersonating employees to gain insider-level access. They use social engineering to trick employees into handing over access credentials such as passwords, or manipulating 2FA and MFA access from the employee. Once inside, they are able to view and modify a wide range of resources.
Take the 2022 Duo breach, where Russian state sponsored attackers exploited MFA protocols, allowing them to enroll an MFA device and access the network. This breach led to the exploitation of a PrintNightmare vulnerability, enabling access to cloud and email accounts for document exfiltration. The was hard to detect because the attackers had valid access credentials, and therefore standard ITDR (identity threat detection and response) tools didn’t work since authentication was already bypassed. From ServiceNow’s perspective as an application, the attackers were valid users with valid credentials, not attackers who are breaking in.
ServiceNow Malicious Insider Scenario
Rogue Employees
Another common ServiceNow scenario involves rogue employees who intentionally want to cause harm to their company. They may be looking to expose sensitive data or steal it and sell it to a competitor.
Without an intrusion, the detection of this is extremely difficult. Strategies such as searching for failed login attempts or parsing access log files for unusual login patterns won’t typically reveal the malicious insider.
Insider Threats
Insiders taking advantage of their rights in corporate enterprise applications to perform malicious operations in business processes:
- Careless employees misusing internal business assets
- Internal fraud in custom-built business applications
- An insider agent stealing information on behalf of outsiders
- An employee accessing data not meant for them (different accounts, branches, countries)
- Data modification, or malicious acts by a disgruntled employee
- Detecting anomalies for 3rd parties via API
Impersonation
Attackers impersonating legitimate users and performing malicious activities:
- Stolen credentials or credential stuffing
- Bypassing MFA
Attackers focused on privileged users for cloud platform and SaaS applications:
- Corporate SaaS applications – attackers impersonate an employee/administrator
- Customer facing portals – attackers impersonate a customer or partner
ServiceNow Breaches: The Threat is Real
According to security researchers, 70 percent of ServiceNow instances are leaking data. This means that attackers or malicious insiders who have gained access to certain types of information can also access sensitive data that should not be viewable to them.
The fact that attackers have stolen hundreds of ServiceNow access credentials only exacerbates the problem. Even if you do manage to configure ServiceNow securely, credentials that fall into the hands of attackers could compromise your resources.
The Limitations of Standard ServiceNow Security
Traditionally, strategies for securing ServiceNow and similar platforms have come up short.
The most common strategy is to use rule-based alerting systems that scan logs in an attempt to detect malicious access and anomalies. This approach is not ideal for two reasons. Firstly, writing the rules requires an enormous amount of effort, which could take months especially for complex ServiceNow instances and sets of integrations. By the time the rules are written, they’re often out of date. Secondly, rule-based detection often results in hundreds of alerts per day, many of which are false positives. This leaves teams with little actionable information about where ServiceNow security risks and malicious insider threats actually lie and where action is required.
Another inadequate approach to securing ServiceNow is to rely on User and Entity Behavior Analytics (UEBA), which aims to detect anomalous behavior. The problem with this solution is that not all users conform their behavior to statistical models. UEBA may catch major deviations from standard user behavior, but it doesn’t work well when dealing with malicious insiders who closely observe and copy the activity of non-malicious users. It doesn’t look at sequences of actions and therefore misses anomalous activity frequently.
ServiceNow supports a number of integrations and connections with SaaS applications and more, making conventional security strategies harder to effectively use. If companies have hundreds of different applications connected to ServiceNow, they’ll need different rules for each one. That approach just doesn’t scale, and it doesn’t deliver accurate and actionable results.
Detecting Malicious Insiders on ServiceNow
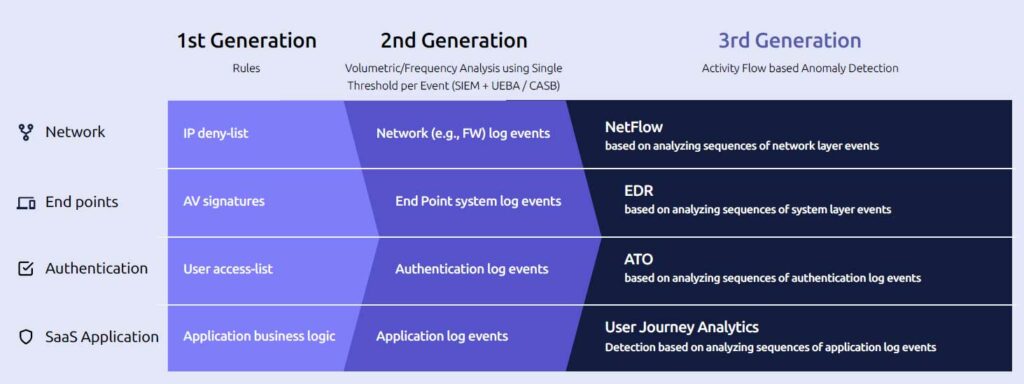
There’s a better approach to protecting ServiceNow data from malicious insiders. It hinges on analyzing all aspects of the entire user journey to gain as much context as possible about what’s normal behavior and what’s a deviation. Under this approach, security teams get far fewer false positives than they would from analyzing logs alone.
Companies also get the ability to detect attackers and malicious insiders on any type of application or resource, regardless of its configuration. Teams don’t need to write custom rules to gain effective protection.
Threat detection models are automatically trained and updated using log data to make them even more accurate. Logs can be historical, or they can get fed into the detection engine in real time.
This approach results in just one or two high fidelity alerts per week, instead of hundreds of false-positives that are mostly “noise,” contributing to alert fatigue. Including sensitivity scores in the solution enables security teams to prioritize alerts to successfully and efficiently remediate vulnerabilities.
A Malicious Insider Detection Success Story
Using this unique ubiquitous approach to malicious insider threat detection, RevealSecurity’s TrackerIQ successfully identified an employee at an insurance company who made changes to beneficiaries’ policies in order to withdraw money from them. TrackerIQ identified 30 instances of suspicious user journeys over a 24 month period. Of those, 6 were identified as the employee who had committed fraud. RevealSecurity discovered that small monetary values of a few cents were moved as far back as 6 months before the final fraud. If this had been continuously monitored, the suspicious behavior would have been identified at a much earlier stage and the final fraud avoided.
In short, conventional approaches to protecting ServiceNow instances from malicious insiders only go so far. By compiling profiles of normal user activity based on the complete operations of all of the organization’s employees, TrackerIQ identified the malicious insider activities as anomalous.
TrackerIQ was built to solve this problem. By taking a different approach to threat detection – on the basis of comprehensive user journey analytics – TrackerIQ provides actionable detection that other tools do not.
Contact RevealSecurity to learn more about how TrackerIQ can help secure your resources in ServiceNow and other business applications.





