This is the first in a three part series taking a look at the rise of pre-emptive identity security and the need to detect and disrupt adversarial attack activity before it completes.
Identity as an Attack Vector
➔ More Identities, More Systems
➔ Internal & External Adversaries
➔ Likelihood and Impact Increasing
Our identity and access management (IAM) infrastructure has rapidly become the main strategic fulcrum for organisational change. IAM today empowers a range of productivity, compliance, security and technological transformation use cases for a range of identity types. From standard employees, contractors and business partners to workloads, non-human identities and autonomous credentials.
However, it is now constantly under attack. From external adversarial activity driven by nation station strategic aims, to insider threat activity and even the subtle combination of external attackers mimicking insider behaviours – every aspect of the identity infrastructure lifecycle faces disruption.
The basic building blocks of IAM infrastructure are typically considered to be identity provider (IDP) and strong authentication, identity governance and administration (IGA), privileged access management (PAM) and some level of policy based access control (PBAC). However, even with the core building blocks in place, organisations of all sizes are still facing data breaches, ransomware, identity theft
and more. Why?
Isolated identity components, a lack of broad end to end coverage for all applications and services and a lack of visibility of identity activity all contribute. These concerns are being amplified by the varied nature of application deployment landscapes too. The common pattern of hybrid environments that consist of on-premises, cloud service provider (CSP), software as a service (SaaS) applications and private cloud-native deployments increase both the identity attack surface, but also introduce visibility issues and broken fulfillment problems.
The secondary issue and the one that is likely to alter both architectural design choices and technology funding patterns, is that the impact of getting IAM “wrong” is considerably larger than it was say a decade ago. The historically tactical and operational focus of B2E workforce identity was often limited to directory services, access request management, access review and basic connectivity and fulfillment use cases. The impact of any of these components being unavailable or degraded was often merely associated with productivity – such as delayed access changes or slow downs in employee onboarding.
Today, getting IAM “wrong” has material impacts for compliance, business enablement and the effectiveness of a range of orthogonal technologies such as data security, endpoint security and more. There are more assumptions on IAM working effectively due to the increased level of technical integrations and the demands being placed upon it.
Weaknesses in Existing IAM Infrastructure
➔ Isolation and Disconnection
➔ Limited Monitoring and Visibility
➔ Lack of Enterprise Stack Focus
However there are some fundamental weaknesses within our traditional IAM world that are hindering both adoption of new technologies (think AI, cloud and mobile) as well as the core risk management and security tenets of the modern enterprise.
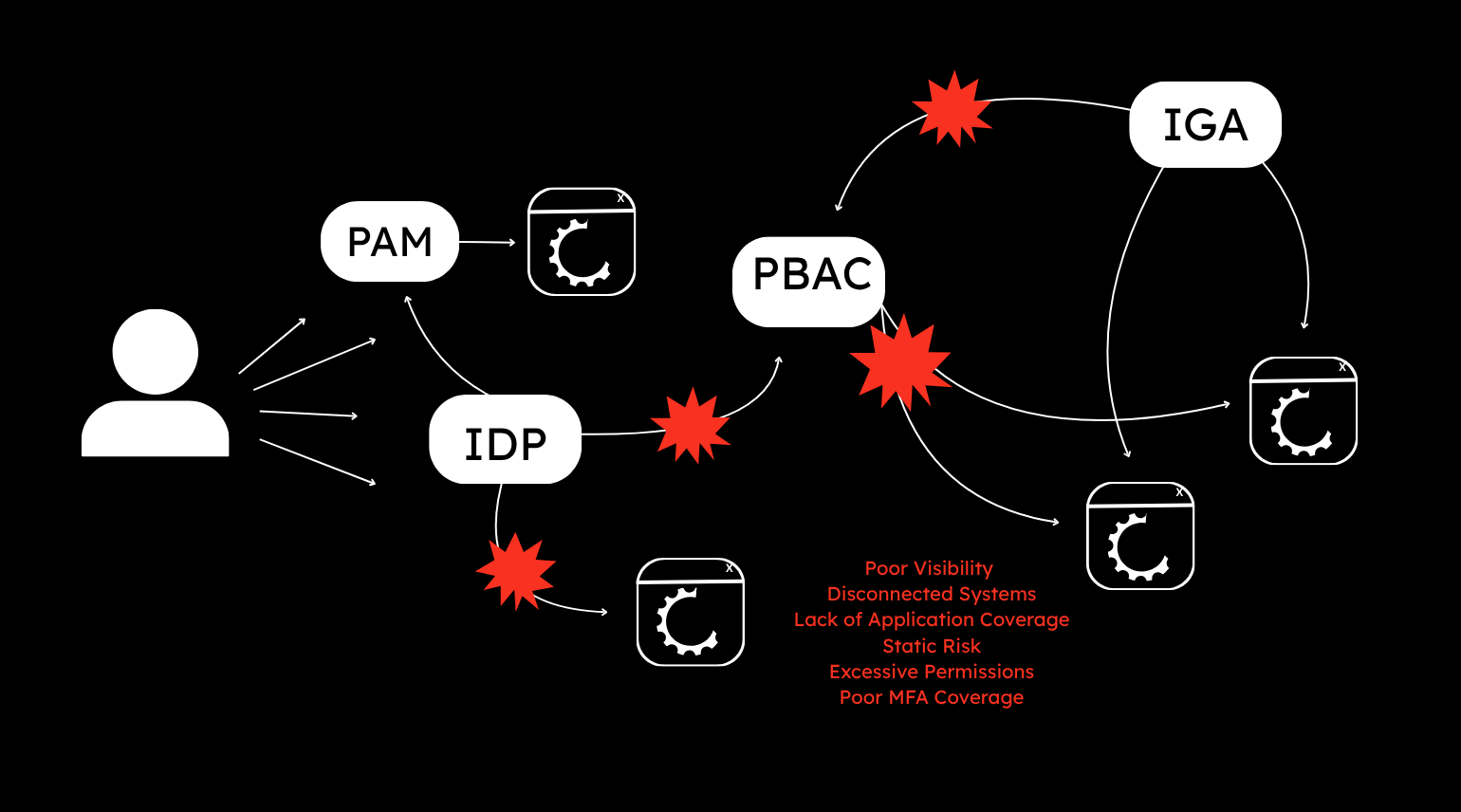
The core IAM capabilities are often disconnected from one another – not just technically but also from a risk and response perspective. Boundaries of responsibility tend to focus on concepts like token issuance, verification and validation, session management and policy enforcement – but a lack of context often hampers informed decision making with respect to access control and risk assessment. The result? Blindspots, an inability to analyse and respond to risky events and a retrospective approach to threat – likely reliant on logs that have been written to after an issue has occurred.
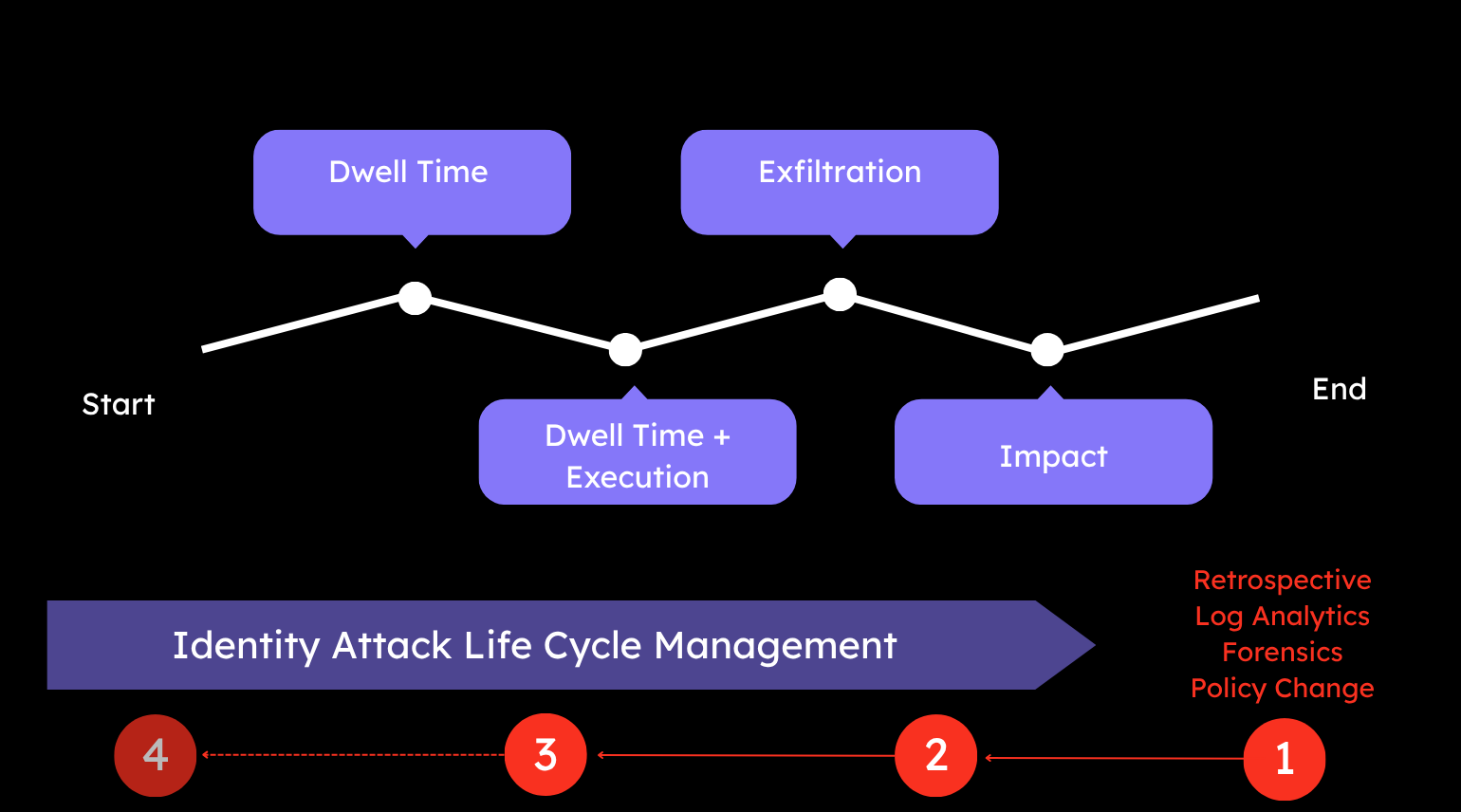
This results in many organisations operating at point 1 on the above schematic. IAM attack management really is more focused upon recovery – as the attack has already completed and the impact sorely felt. At best, a deep dive forensics investigation can result in changes to access and authentication policy, perhaps also the removal of accounts or permissions that were used.
Strategically, organisations need to start moving left of this point and ultimately “left of boom” entirely, getting ahead of the attackers and implementing disruption and response tactics before the attack completes. Here we are focused on getting to points 2 and 3 over time, by understanding that firstly an attack is taking place and in turn make a decision at some point to interrupt the attack with a set of disruptive tactics. These tactics could include redirection to a honeypot, reduction in session life time, removal of permissions and so on.
Ultimately we are aiming to materially impact the mean time to detection (MTTD) and mean time to recovery (MTTR) metrics associated with the attack chain which allows organisations to strategically move to a pre-emptive attack posture.
Why This Matters
➔ Google M trends
➔ Salesloft
➔ Rise of AI
The recent Google Mandiant M-Trends report provides an annual overview of cyber incidents impacting the global economy. The word “identity” appears 96 times in the 2025 report. For example, stolen credentials has now overtaken phishing attacks as the second most used initial infection vector. From a cloud compromise point of view, “identity solutions that lack sufficient security controls” was the number one theme of attack. Integration challenges and poor policies between on-premises directories, federated identity providers and cloud services is another example where vulnerabilities are being exploited without appropriate monitoring or detection capabilities.
The recent Salesforce data breach that leveraged Saleloft Drift was based upon malicious usage of OAuth2 access tokens. Data exfiltration was also focused upon further credential search and harvesting techniques. Improved security segmentation and IP-origin binding associated with token use could have helped in this situation along with ways to monitor suspicious activity focused on credential queries and searches.
There are numerous examples of identity-centric attacks being carried out against both human and non-human identity infrastructures – across all sectors of the global economy. As many organisations are still transitioning to a more zero-trust “access anything anywhere” design pattern, where borders are porous and resources exist everywhere, adversaries are already there. They understand that by targeting identities, accounts, sessions and the access paths these components leverage to use and share data or complete transactions are the most rewarding vector to complete sophisticated attacks.
Isolated endpoint, network and single-system monitoring using specific rules and “tripwires” are vastly redundant in this identity-centric world. The rise of AI as both an adversarial tool, but also an unmanaged productivity enabler opens up new attack vectors where identity and access management vulnerabilities are exploitable.
Organisations need to first understand their identity-centric landscape and infrastructure before undertaking identity vulnerability analysis that can help identify the impact and likelihood of these types of attacks. By attempting to move “left of boom” organizations can strategically move towards a pre-emptive position which improves security response and reduces risk.









