Detect attacks in your SaaS applications
Continuously monitor SaaS usage to accurately detect and respond to suspicious activity
Book a Demo
Security Gap: Identifying malicious activity in SaaS applications
Current detection solutions including SaaS detection solutions were built to prevent identity attacks at or prior to the point of login. They lack insight into identity behavior within SaaS applications and do not offer effective detection of suspicious or malicious activities after login.
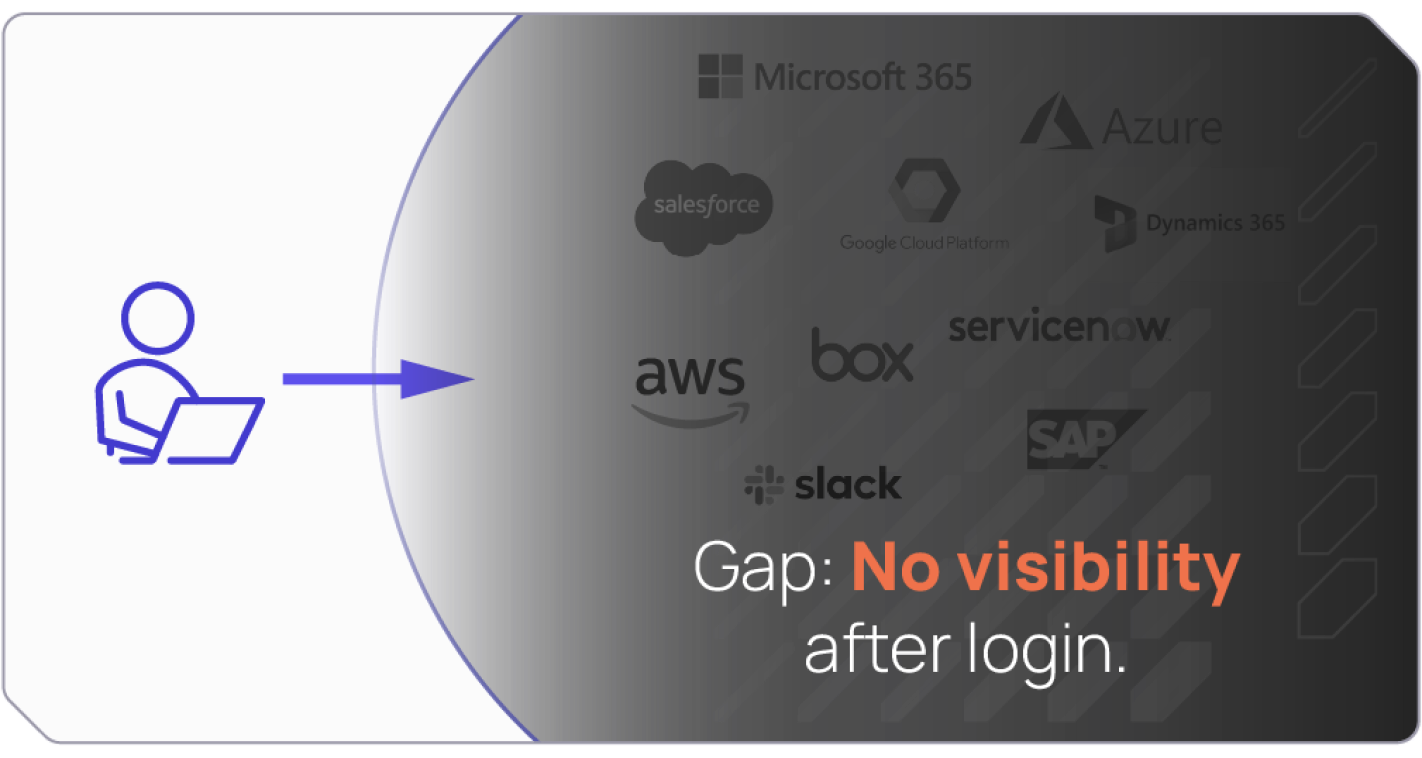
Unmonitored SaaS applications pose security risks
Current detection solutions like SIEM rule-based detection and UEBA are focused on infrastructure layers and offer very minimal detection for SaaS applications. The SaaS detection capabilities offered by SIEM and UEBA are focused on the pre-login mainly to detect stolen credentials but are blind to the activity of authenticated identities. This poses a critical security risk, including:
Reveal Security: Accurate Detection for SaaS Application Misuse and Abuse
The Reveal Security platform continuously monitors the behavior of human and machine identities in your SaaS applications. The platform accurately detects suspicious activities that usually indicate misuse or abuse of the application that can lead to data leakage or business harm.
Reveal Security is the only solution that has patented Identity Journey Analytics™ technology, powered by unsupervised machine learning, that creates profiles of typical identity journeys and then compares new journeys to them to accurately detect anomalous journeys. This ML-based anomaly detection technology delivers high-fidelity alerts with clear context and very few false positives, streamlining incident response.
Works seamlessly with any SaaS application


![]()
![]()
![]()

![]()
Have a specific SaaS app or cloud service you want to monitor?
View more
SOLUTION BRIEF
Reveal Security for AWS
Monitor Privileged User Behavior and Detect Suspicious Activity with ML-Based Detection
Download
SOLUTION BRIEF
Reveal Security for Salesforce
Detect threats in Salesforce by malicious insiders, administrators, API usage, and imposters.
Download
SOLUTION BRIEF
Reveal Security for Microsoft 365
Detect Malicious Activity in Microsoft 365 to Prevent Data Theft
Download
SOLUTION BRIEF
Reveal Security for Okta
Monitor Okta Users to Quickly and Accurately Detect Account Takeover and Insider Threats
Download
SOLUTION BRIEF

